Cyber Security Awareness
Preface
Principal, the purpose of this cyber security awareness page is just to provide information on cyber security awareness, with a fragment of virtual private network and encryption.
Together with mentioned, there is also a link to reputable open-source online certification, to test the knowledge on cyber security awareness for personal benefit or as an idea for potential professional opportunity.
Every part of the information provided is in summarized form, in conjunction, a few selected resources to complement a subject from different professional points to anyone requiring it or just for leisurely pursuit of knowledge.
Essential
At present, it is the fact that cyber-attacks are more common and, for some, even daily occurrence. Companies and public institutions continuously search for new approaches for cyber security awareness campaigns. Reason for this is that individuals or employees, still either are not aware or do not perceive the risks. That they can (unintentionally or intentionally) expose themselves and others to various cyber and other interconnected problems.
As well, people can and are tired of security procedures and processes, especially if they perceive security as an obstacle, preventing them from their primary task. And with addition of constant emphasis to remain highly vigilant to security awareness––described as security fatigue.1, 2
In the same way is true, that primary purpose of cyber security awareness campaigns is to influence. Adopting secure and responsible behavior in an online environment for the individual, employees and businesses together whole. But therefore sterile transfer of knowledge about good practices in cyber security awareness and cyber security is sometimes far from adequate.3
Cyber awareness is a prerequisite for good cyber security. But to become a part of an organization or individual’s practice and second nature, it takes far more self-discipline. Therefore, an abridged recap list of universally highlighted main cyber security awareness points that are equivalently useful for individuals and business alike, are still fundamental requirement.
Abridge list of cyber security awareness points4,5
Back up your data
By backing your data to a separate location, where can be retrieved is the simplest and important thing you can do for yourself or your business. After all, backups to be effective need to be protected from unauthorized access by combined encryption and physical protection.
Keep your devices up-to-date and protected, with antiviral software
Keep software on all devices up-to-date, since updates simultaneously add new features, but also fix vulnerabilities that halt attackers from getting access to your computer or business network. Also, you need to have powerful antiviral software that is up-to-date and capable of efficiently protecting the hardware as-well-as software or the entire business system network.
Unique passwords and two-factor authentication
Create strong passwords for anything that needs password protection and use an assorted and unique password for every online account you create. Whereas, any default passwords found in software or elsewhere should be changed immediately. Another way to protect your online accounts being hacked, you can decide to activate two-factor authentication for your important accounts, such as your email and social media accounts.
Social media smart, online personal information and sensitive transaction on free WiFi
We are used to posting information on social media and sharing things online that we do not think about it anymore. However, by posting or sharing on social media, we should know that information could be used against you or business. Through way of stealing your identity or hacking into your online accounts or business network. By limiting personal information, you can lower the possibility of scams, frauds and other tricks, which harm you or your business personally and financially.
Bank statements and financial details
Verifying bank statements is vital to notice any unauthorized transfer of funds in your bank account or unexpected charges to your credit or debit card. Therefore, someone has access to your accounts or credit card information. In the same way, businesses should double check any questionable or unexpected requests for a financial transaction or change of bank details. This is the first sign that someone is attempting to scam or defraud the company––so any unexpected or unusual requests should be additionally approved.
End supplement to Cyber Security Awareness—Virtual Private Network & Encryption
Basics portrayal
Virtual Private Network or VPN reign is being described professionally as ‘uniquely enduring’. It could be understood as something that is outdated, which is close to the truth within the digital realm. It is a persistent and growing part of digital security, which reinforces online privacy. Its guarded strength rests on components of encryption protocols, ciphers, and tunnel transmission.6
Encryption and cryptography, cryptography and encryption
Throughout the history, various methods of encryption have been used to aid in cryptography. A succinct description formulates cryptography as the practice and study of techniques about constructing and analyzing protocols for secure communication, which prevents third parties from reading non-public messages. And encryption is the process of encoding information in cryptography.7,8 Encryption as a process which converts the original information, known as plain-text, into an alternative form known as cipher-text using algorithm codes and keys. If possible, only allowed parties can decipher a cipher-text back to plain-text, if they have the right code and key to access the original information.9
Virtual private network and general functioning
Any use of VPN should mean encryption of all the traffic going in and from your device at each end of the tunnel. However, for VPN to be effective, the encryption is a core component that may be applied before original information is transmitted through the tunnel. That enables secured encrypted information traffic between sender and receiver. Even so, VPN to be considered secure, the participants need to have oversight at both ends of the entire data path, or the content is encrypted before it enters the tunnel provider. PureVPN commercial provider is an example that is considered safest and, as already mentioned, encrypts before all outgoing and incoming traffic is tunneled through an intermediary server. This process allows if traffic is purposely intercepted, that it would be unreadable. For the encryption part, PureVPN uses 256-bit encryption and possibility of protocol. For effective digital security and privacy, a combination of different software (for instance, Tor), with layered encryption, is needed to reach protection of superior level. But then again, it also needs to be understood that combination can have a decreased or increased effect on security and protection. Therefore, nothing is simple when it comes to a superior level of digital encryption and protection.9,10
Assortment list of VPN encryption, ciphers, protocols and general functioning
When you consider increasing personal or business online protection, there are three things in VPN that influence your decision. One is type of encryption; the other is encryption protocol and the third part is just as important as the first two––cipher. What each brings and how it works inside VPN is a comprehensive scope. Still, added list will facilitate in part of further information search for details and that preferred affinity for understanding of superior level in digital protection.11,12,13,14,15
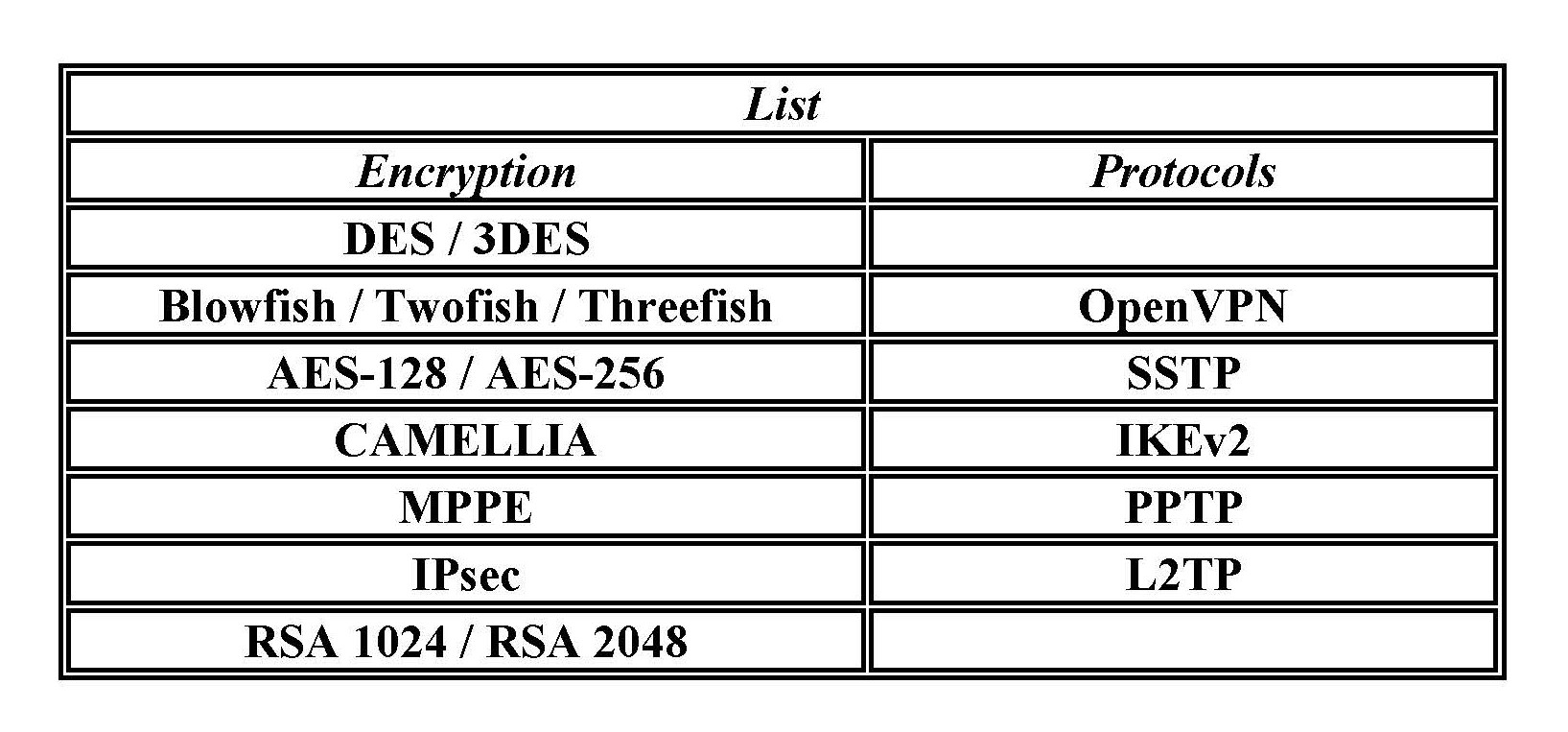
But before searching for all these details begins; there are two approaches for encryption and decryption for sent data that is based on protocols opted by the users. One is asymmetric encryption or public-key cryptography that uses two keys––public key and a private key for encryption and decryption. And symmetric encryption or pre-shared key encryption that uses a single key to both encrypt and decrypt data. As already mentioned, encryption has a task to encrypt data. The protocol determines how your data should pass through your computer and VPN servers. And third is cipher––an algorithm that performs the encryption. The strength of a cipher depends on both the key length and the strength of the algorithm. Key length indicates the quantity of bits involved and cipher is the algorithm that encrypts. The larger the key length, the more calculations are involved. Therefore, more processing power is required. This affects how fast data can be encrypted and decrypted. For this reason, commercial VPN is a negotiated balance between protection and usability.9,11,16
Final thought––when it comes to digital security, recommendations are now arriving on a daily if not hourly basis. The most interesting of those it borrow openly from governmental books––idea is that all companies are to establish a policy of digital travel pre-approval, if travel is deemed risk to business––electronic devices carried should be on loan or specialized. And upon return, they should be immediately formatted. On the end in this overflow of information and recommendations, individuals and business are left again to find the balance to superior level of digital protection and watch for security fatigue.1,17
Final version: 26 March 2021
Updated: 17 April 2023
Search about Cyber Security Awareness and Virtual Private Network & Encryption through bibliography list for further reading.
References
1. NIST – National Institute of Standards and Technology. 2016. Security Fatigue Can Cause Computer Users to Feel Hopeless and Act Recklessly, New Study Suggests. Retrieved from: https://www.nist.gov/news-events/news/2016/10/security-fatigue-can-cause-computer-users-feel-hopeless-and-act-recklessly or Stanton, B., et al. 2016. Security Fatigue. IT Professional. Volume: 18, Issue: 5. Retrieved from: DOI: 10.1109/MITP.2016.84 (01/12/2020)
2. Bada, M. Sasse A. and Nurse, J. 2014. Cyber Security Awareness Campaigns Why do they fail to change behavior? Retrieved from: https://arxiv.org/abs/1901.02672 or (01/12/2020)
3. ISF – Information Security Forum. 2014. From Promoting Awareness to Embedding Behaviours: Secure by choice, not by chance. Retrieved from: https://www.securityforum.org/research/from-promoting-awareness-to-embedding-behaviours/ (01/12/2020)
4. CERT NZ. 2020. Individual. www.cert.govt.nz Retrieved from: https://www.cert.govt.nz/individuals/ (01/12/2020)
5. CERT NZ. 2020. Business. www.cert.govt.nz Retrieved from: https://www.cert.govt.nz/business/ (01/12/2020)
6. Tennent, C. 2019. The ultimate guide to VPN encryption, protocols, and ciphers. cybersecurity.att.com. Retrieved from: https://cybersecurity.att.com/blogs/security-essentials/the-ultimate-guide-to-vpn-encryption-protocols-and-ciphers (10/03/2021)
7. Ayesh, S. and Dweib, M. 2016. SMA Cryptography Algorithm Decrypt MD5 Solution. International Journal for Advance Research. 4(11), 290-296. Retrieved from: http://dx.doi.org/10.21474/IJAR01/2081 (10/03/2021)
8. Bellare, M. and Rogaway, P. 2005. Introduction to Modern Cryptography. Retrieved from: https://web.cs.ucdavis.edu/~rogaway/classes/227/spring05/book/main.pdf (10/03/2021)
9. Akhtar, A. 2020. What is VPN Encryption & How Does it Work? www.vpnranks.com. Retrieved from: https://www.vpnranks.com/resources/what-is-vpn-encryption/ (10/03/2021)
10. Anon, D. 2018. Best free encryption software: 35+ free tools. privacy.net. Retrieved from: https://privacy.net/best-free-encryption-software-tools/ (10/03/2021)
11. Allan, M. 2019. 6 Types of Encryption That You Must Know About. www.goodcore.co.uk. Retrieved from: https://www.goodcore.co.uk/blog/types-of-encryption/ (10/03/2021)
12. Patila, P. et al. 2016. A Comprehensive Evaluation of Cryptographic Algorithms DES, 3DES, AES, RSA and Blowfish. www.researchgate.net. Retrieved from:https://www.researchgate.net/publication/301234351_A_Comprehensive_Evaluation_of_Cryptographic_Algorithms_DES_3DES_AES_RSA_and_Blowfish/link/5738f6fd08ae298602e2b2cd/download (10/03/2021)
13. Wahid, M. et al. 2018. A Comparison of Cryptographic Algorithms: DES, 3DES, AES, RSA and Blowfish for Guessing Attacks Prevention. Journal of Computer Science Applications and Information Technology. symbiosisonlinepublishing.com Retrieved from:https://www.semanticscholar.org/paper/A-Comparison-of-Cryptographic-Algorithms%3A-DES%2C-AES%2C-Wahid-Ali/6133bb355672b8a6c4f1c410bc41abc6a94162a7 (10/03/2021)
14. Schneier, 1994. B. Description of a New Variable-Length Key, 64-Bit Block Cipher (Blowfish) www.schneier.com Retrieved from: https://www.schneier.com/academic/archives/1994/09/description_of_a_new.html (10/03/2021)
15. Jeevalatha, E. and SenthilMurugan, S. 2018. Evolution of AES, Blowfish and Two fish Encryption Algorithm. International Journal of Scientific & Engineering Research Vol. 9, Issue 4, April 2018. Retrieved from: https://www.ijser.org/researchpaper/Evolution-of-AES-Blowfish-and-Two-fish-Encryption-Algorithm.pdf (10/03/2021)
16. Digicert. 2021. Behind the Scenes of SSL Cryptography. Retrieved from: https://www.digicert.com/ssl-cryptography.htm (10/03/2021)
17. IDG News Service. 2021. Seven critical IT policies you should have in place. www.techcentral.ie. Retrieved from: https://www.techcentral.ie/seven-critical-it-policies-you-should-have-in-place/ (10/03/2021)
Further Reading
A. DNV-GL. 2020. Maritime cyber security. Retrieved from: https://www.dnvgl.com/maritime/insights/topics/maritime-cyber-security/ism-guidance.html (01/12/2020)
B. DNV-GL. 2020. Recommended practice: Cyber security resilience management. Retrieved from: https://www.dnvgl.com/maritime/dnvgl-rp-0496-recommended-practice-cyber-security-download.html (01/12/2020)
C. DNV-GL. 2020. Maritime Cyber Security Awareness E-learning. Retrieved from: https://www.dnvgl.com/maritime/maritime-academy/cyber-security-elearning.html (01/12/2020)
D. IMO – International Maritime Organization. 2019. Maritime cyber risk. Retrieved from: https://www.imo.org/en/OurWork/Security/Pages/Cyber-security.aspx (01/12/2020)
E. ISO – International Organization for Standardization. 2013. ISO/IEC 27001 - Information security management. Retrieved from: https://www.iso.org/isoiec-27001-information-security.html (01/12/2020)
F. NIST – National Institute of Standards and Technology. 2018. Cybersecurity Framework. Retrieved from: https://www.nist.gov/cyberframework (01/12/2020)
G. Wilson, M. and Hash, J. 2003. NIST: Building an Information Technology Security Awareness and Training Program – Computer Security. Retrieved from: http://csrc.nist.gov/publications/nistpubs/800-50/NIST-SP800-50.pdf (01/12/2020)
H. Richardson, R. 2008. 2008 CSI Computer Crime and Security Survey. Retrieved from: http://i.cmpnet.com/v2.gocsi.com/pdf/CSIsurvey2008.pdf (10/03/2021)
I. Nikitin, K. et al. 2019. Reducing Metadata Leakage from Encrypted Files and Communication with PURBs. Retrieved from: https://petsymposium.org/2019/files/papers/issue4/popets-2019-0056.pdf (10/03/2021)
J. Solenov, D. Brieler, J. and Scherrer, J. 2018. The Potential of Quantum Computing and Machine Learning to Advance Clinical Research and Change the Practice of Medicine. Retrieved from: https://www.ncbi.nlm.nih.gov/pmc/articles/PMC6205278/pdf/ms115_p0463.pdf (10/03/2021)
K. Emerging Technology from the arXiv. 2010. 1978 Cryptosystem Resists Quantum Attack. MIT Technology Review. Retrieved from: https://www.technologyreview.com/2010/08/18/26136/1978-cryptosystem-resists-quantum-attack/ (10/03/2021)
L. Emerging Technology from the arXiv. 2019. How a quantum computer could break 2048-bit RSA encryption in 8 hours. MIT Technology Review. Retrieved from: https://www.technologyreview.com/2019/05/30/65724/how-a-quantum-computer-could-break-2048-bit-rsa-encryption-in-8-hours/ (10/03/2021)
M. Rivest, R. Shamir, A. and Adleman, L. 1978. A Method for Obtaining Digital Signatures and Public-Key Cryptosystems. Retrieved from: https://web.archive.org/web/20011116122233/http://theory.lcs.mit.edu/~rivest/rsapaper.pdf (10/03/2021)
N. Eriksson, M. (2003). An Example of a Man-in-the-middle Attack against Server. Retrieved from: http://www8.cs.umu.se/education/examina/Rapporter/MattiasEriksson.pdf (10/03/2021)
O. NIST – National Institute of Standards and Technology. 2001. Advanced Encryption Standard (AES). Federal Information Processing Standards Publication 197. Retrieved from: https://web.archive.org/web/20150407153905/http://csrc.nist.gov/publications/fips/fips197/fips-197.pdf (10/03/2021)
P. Smart, N. (2004). Cryptography: An Introduction. 3th Edition. Retrieved from: http://www.cs.umd.edu/~waa/414-F11/IntroToCrypto.pdf (10/03/2021)
Q. Network Associate 1998. An Introduction to Cryptography (PGP). Retrieved from: http://cisweb.bristolcc.edu/~ik/Download/CIT18/IntroToCrypto.pdf (10/03/2021)
R. Rivest, R. 1991. Cryptography and Machine Learning. Retrieved from: https://people.csail.mit.edu/rivest/pubs/Riv91.pdf (10/03/2021)
S. Menezes, A. et al. 1996-97. Handbook of applied cryptography. Retrieved from: https://doc.lagout.org/network/3_Cryptography/CRC%20Press%20-%20Handbook%20of%20applied%20Cryptography.pdf and https://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.99.2838&rep=rep1&type=pdf (10/03/2021)
T. Katz, J. and Lindell, Y. 2015. Introduction to Modern Cryptography. Retrieved from: https://eclass.uniwa.gr/modules/document/file.php/CSCYB105/Reading%20Material/%5BJonathan_Katz%2C_Yehuda_Lindell%5D_Introduction_to_Mo%282nd%29.pdf (10/03/2021)
U. Cormen, T. et al. 2009. Introduction to Algorithms. Third Edition. The MIT Press Cambridge, Massachusetts. Retrieved from: https://edutechlearners.com/download/Introduction_to_algorithms-3rd%20Edition.pdf (10/03/2021)
V. Ferguson, N. et al. 2010. The Skein Hash Function Family. Retrieved from: https://www.schneier.com/wp-content/uploads/2016/02/skein.pdf (10/03/2021)
W. Lovecruft, I. 2016. Tor's Circuit-Layer Cryptography: Attacks, Hacks, and Improvements. University of Waterloo. Retrieved from: https://web.archive.org/web/20161019151220/https://people.torproject.org/~isis/slides/2016-10-13-waterloo-handout.pdf (10/03/2021)